These days, the internet is the lifeblood of contemporary businesses. But that goes hand in hand with a risk: an epidemic of cyberattacks. Cyberthieves are becoming increasingly sophisticated and are employing advanced tactics such as phishing and ransomware to prey on businesses. Conventional security measures, like firewalls and VPNs, simply can't keep pace with the realities of remote work—this is where Zero Trust Security becomes essential. Solutions like Cloudflare Zero Trust offer a smarter, more modern approach to protecting digital infrastructure by verifying every user and device before granting access.
Why Old Security Models No Longer Work 😰
In the old days, businesses employed a "castle-and-moat" security model. Once inside the network, they trusted anyone. But that is dangerous. If a hacker tricks one employee, they might have access to all.
To understand the evolution of internet security and how digital infrastructures can be hardened, this article on why cloud-era cybersecurity matters provides a solid foundation.
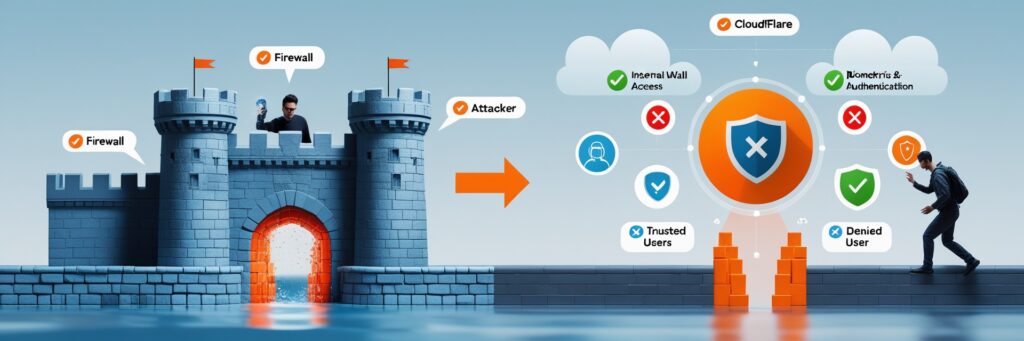
Introducing Zero Trust Security 😀
Zero Trust is a different case. Zero Trust has one simple but effective principle: "Never trust, always verify." It involves checking all users and devices each time they attempt to access something. It doesn't matter whether they are within or outside of the company network.
What is Cloudflare Zero Trust? 🤔
Cloudflare Zero Trust makes this new security concept a reality. It provides businesses with means to protect access to their apps without using traditional VPNs. And the best part is? It's more affordable and simpler than you may believe.
Key Components of Cloudflare Zero Trust
✅Cloudflare Access: Verifies users before they can access any company app.
✅Cloudflare Gateway: Protects internet surfing.
✅DNS Filtering: Prevents malicious websites
✅Browser Isolation: Secures sensitive information through web browsing isolation
✅Device Checks: Ensures trusted devices are the only ones allowed to access resources
✅Single Sign-On: Integrates with login platforms such as Google Workspace and Azure AD
Implementing Zero Trust with Cloudflare
Starting out is easier than you'd think:
👉 If you're unsure where to begin, check out this complete step-by-step guide to set up Cloudflare for hands-on instructions tailored for beginners.
Log in to the Cloudflare Zero Trust Dashboard.
Configure teams and rules.
Integrate your login system.
Configure access for your apps.
Configure web filtering.
Enable Browser Isolation if you wish for additional protection.
Monitor and improve things.
Advantages of Cloudflare Zero Trust and Zero Trust Security
Improved Security Posture
Intelligent Access Control: Cloudflare Zero Trust enables organizations to implement granular access controls, which allow only trusted users and devices to access sensitive information.
Multi-Factor Authentication: Inclines towards advanced authentication techniques such as biometrics and password-less authentication, making it more difficult for attackers to access systems without permission.
Network Segmentation: Restricts access of users and devices to certain resources, lowering the threat of a data breach.
End-to-End Encryption: Encrypts data in transit and at rest so that even if breached, data is still unreadable.
Simplified Remote Access
VPN Replacement: Cloudflare Zero Trust obliterates the need for traditional VPNs by authenticating identity for single applications, providing faster and more secure access for remote employees.
Secure Remote Access: Shields remote employees, contractors, and partners from threats by locking down access to internal assets.
Browser Isolation: Runs browser code in the cloud to shield against dangerous websites while preserving a smooth user experience.
Enhanced Productivity
Single Sign-On (SSO): Enables users to access numerous apps using a single set of credentials, streamlining login processes and eliminating password fatigue.
Faster Onboarding: Rapidly deploys least-privilege access to new hires or third-party users without the need for additional infrastructure such as VPN capacity.
Self-Service Portal: Enables users to control their own access and password reset without IT assistance, enhancing productivity while lowering IT overhead.
Unified Security Management
Centralized Management Console: Offers IT administrators a single console to manage policy for all devices and users, simplifying operations and enhancing efficiency.
Integration with Other Tools: Integrates well with third-party solutions such as firewalls, identity providers (e.g., Okta, Azure AD), and SIEM tools for end-to-end security coverage.
Compliance and Visibility
Regulatory Compliance: Enables organizations to comply with data security laws like GDPR, HIPAA, and SOC 2 by strictly enforcing security policies.
Detailed Reporting & Analytics: Provides visibility into security events, allowing proactive risk management and compliance monitoring.
Cloud Workload Visibility: monitors employee usage of cloud apps in order to eliminate shadow IT as well as better smarten up cloud investments.
Scalability and Performance
Global Edge Network: infrastructure is provided by Cloudflare such that there will be low latency, high availability for even world-spread teams.
IoT Security: Secures Internet of Things (IoT) devices beyond the human-based ones under an integrated environment.
Data Loss Prevention (DLP): Identifies sensitive information in transit or at rest within SaaS applications to avoid leaks or compliance issues.
Cost Efficiency
Decreases dependence on costly legacy solutions such as VPNs while offering more comprehensive security features.
Simple deployment enables organizations of any size to implement Zero Trust without substantial upfront investment or workflow disruption.
Common Questions (FAQ)
Q: What is Cloudflare Zero Trust, precisely?
A: It's a new method of security that screens everyone prior to allowing them access to apps or data.
Q: How is it different from previous security methods?
A: It screens every access attempt, rather than trusting anyone within the network.
Q: Is it just for large companies?
A: No, it's for businesses of any size.
Q: Do I have to replace all my security equipment to use it?
A: No, it integrates with what you already have.
Q: Can it replace my VPN?
A: Yes, and it's also faster and more secure.
Q: How long will it take to install?
A: You can get the basics done in a few hours. Advanced setup may take a few days.
Wrap-Up: Embrace the Future with Zero Trust
Let's face it: old security methods just aren't cutting it in today's fast-paced digital world. It's time to upgrade your security game with Cloudflare Zero Trust. This isn't just about protecting your business; it's about safeguarding your users, apps, and data in a way that's both secure and seamless.
Imagine Zero Trust as having a really clever personal security assistant. It verifies every access request to make sure that only the right users and devices gain entry. No more trusting old VPNs or fretting about hackers finding their way in.
By going with Zero Trust, you're taking not only security for your digital infrastructure, but you're future-proofing it. You're empowering your workers to work securely anywhere, without giving up performance or speed. And with Cloudflare's edge network around the world, you can expand your protection as your business expands.
What do you have to lose? Engage with Zero Trust today and find the satisfaction that comes from being able to ensure your online resources are under wraps. Discover the Cloudflare Zero Trust Dashboard now and take the first steps in creating a more secure, more robust tomorrow for your enterprise.